In today’s world, risk management and security are front and center topics for every enterprise. And because money is money, the management of payment risk and security has to be a priority.
In this chapter of our Merchant Payment Operations series, we look at top of mind payment and security risks facing today’s enterprises and the essential steps you should consider when improving your controls environment.
As a reminder, the foundation of effective payments risk management is the Money Team. It’s the Money Team’s job to oversee payments functions across the organization. As we will see, because risk management is complex and applies across the entire organization, the organizing role of the Money Team becomes particularly beneficial. The Money Team’s purview extends across all areas of merchant and biller operations. With a cross-functional remit and with representation from across business lines, the Money Team ensures risk management concerns will be addressed holistically.
Read more about the Money Team and its functions here.
What’s Your Risk Profile?
Risk tolerance is highly specific to each enterprise. Each company makes its own determination on how to mitigate risk and where to invest in controls to do so.
It takes a thorough risk assessment process to make those decisions because only through a complete investigation can risk be quantified. A comprehensive risk assessment is necessary to protect your interests. And that is another reason to put the Money Team’s risk experts to work.
In Glenbrook’s payments strategy consulting work, we use the following Payments Risk Taxonomy to lay out the major categories and types of risk to be assessed.
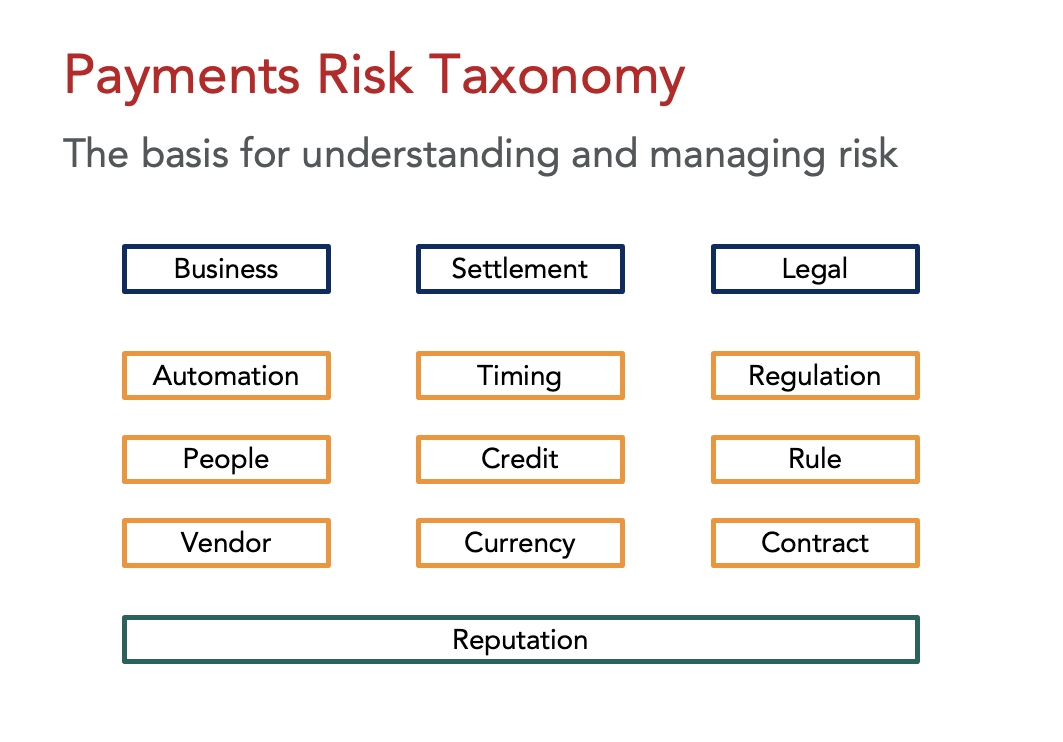
Let’s review the Payments Risk Taxonomy in some detail:
Business Risk
The systems, processes, and people that touch money are components of Business Risk.
Automation Risk. Payments handling is dependent upon automation. Included here are a wide range of IT operational risks ranging from inadequate authentication processes to business continuity in the event of a natural disaster or a pandemic. Think of the deeply systemic role that IT plays to appreciate the myriad ways tech compromise and failure can impact the enterprise. And consider the distributed nature of responsibility for those functions across your organization.
People Risk. People Risk extends well beyond the classic case of the insider enabling external criminal activity. For example, many payments industry companies had to manage the risks of moving thousands of their employees into work from home mode at the COVID-19 pandemic’s beginning. Process changes were required and with changes potential process errors are introduced. Mitigation steps include up-to-date training, regular process reviews and reevaluation, plus incentives that align with risk and security goals. Consider how broadly these roles and responsibilities are distributed across your company.
Vendor Risk. Many payments functions are provided to the enterprise as services by partner companies. These vendors provide essential services but they also introduce risk. Strategies exist to mitigate vendor risk because service level agreements (SLAs) cannot directly address or adequately compensate the company, for an extended service outage, for example
The enterprise must regularly receive evidence of security compliance as well as verified regulatory compliance. Compliance at this level is table stakes for a sound vendor relationship. There are far too many instances of lapses by a partner company impacting their customer’s operations, and ultimately reputation. Vendor risks and controls must be verified during the RFP process and vetted continuously throughout the life of the partnership. Indeed, monitoring vendor compliance is part of the Money Team’s responsibility.
Even with maximum use of third party outsourcing, it is still the Money Team’s responsibility to maintain and improve the firm’s risk management capability. Think broadly about all the vendor relationships you rely on for processing payments. How often are these relationships reviewed from a financial, operational, and reputation standpoint?
Settlement Risk
Access to money and the cost of that access comprise Settlement Risk.
Timing Risk. In treasury management, timing is everything.. Every payment system moves money into and out of the enterprise’s accounts with distinct metrics and associated costs. Should the proceeds of a day’s sales show up a day later than scheduled, the enterprise may be subject to a cash flow shortfall – a painful position to be in if commitments against those funds are in place.
Credit Risk. Payments require two end parties to complete a transaction, and credit risk is the risk that one end party can not meet its obligation to pay. In enterprise payments, these risks can emerge when payment service providers are unable to settle funds to the enterprise’s account. Today when every size business is “going global”, a new sanction or geopolitical hiccup can create credit risk.
Currency Risk. For businesses accepting payments from or initiating payments to another country, currency fluctuations affect transaction profitability. Timing risk adds to the complication of managing cross-border and cross-currency transactions.
Think about the payments your organization accepts. How well do the teams responsible for processing these payments understand settlement risks and the controls required to optimize cash flow and mitigate unfavorable outcomes?
Legal Risk
Legal risk is the risk that the enterprise is in violation of contract terms, government regulations, or operating rules. These violations have ramifications to the enterprise beyond fines and penalties.
Regulation Risk. Municipal, state, national, and international regulations prescribe how payments are handled and funds held. Changes in government regulations can challenge payment operations. New regulations can literally reshape markets. Payments regulations can be direct, specific to a payment transaction process, or indirect, such as data or privacy laws that surround transaction processing.
The ability to comply with and nimbly respond to regulatory change can be optimized through thoughtful technology vendor selection as well as other controls.
Rule Risk. Payment systems operate under a set of business rules to which direct and indirect participants must conform. While indirect participants may not have a contractual relationship to the system operator, they may be subject to the system’s rules as expressed through their contract with the direct system participant. A card accepting merchant does not, for example, have a contractual obligation to Visa or Mastercard. But should one or both of the card networks make a rule change, the merchant’s acquirer will pass the relevant obligations to the merchant. System rules changes can enfranchise a new business model and, as quickly, kill off another.
Contract Risk. Compliance to contract terms is at the center of vendor management. Concerns go beyond delivering on SLAs. Contract terms should require vendor compliance to all applicable rules and regulations. Performance audits are generally necessary to assure contract compliance.
If the vendor falls out of compliance, risk may fall onto the enterprise. While a contract may spell out the remedies should a vendor fail to deliver, those remedies may do little to compensate for the real damage to the business. Mitigating this particular risk may require the use of redundant providers.
Think about the contracts, operating rules, and regulations underpinning your payment operations. How easy is it for your people to gain access to, understand, and implement these obligations?
Focus on the Right Things
Anticipate Change
Resilience in business includes preparation for the unexpected. COVID-19 has revealed how unprepared many businesses were for the shift to “touchless” commerce.
Many businesses have scrambled to add or expand their digital payment capabilities. The surge in new online accounts meant that one in two of these transactions were flagged as high risk. And many of these new to digital channels have been confronted by fraud. Per a NuData report, the increase in ecommerce chargebacks was 36% and the increase for buy online pickup instore (BOPIS) was 124%.
Others who have seen their volume shift to online channels have discovered that fraud detection is now more complex. Good customers have shifted channels. Pandemic induced changes to shipping addresses have been common as people moved to temporary locations. Such changes complicate fraud detection.
[Take a listen to our Payments on Fire® podcast discussing this issue.]
These stats highlight the need to manage all “channels” and technology in an integrated fashion. A strong Money Team and well documented risks and controls make anticipating and preparing for change easier.
Control Risk, Maintain Compliance
Controlling risk is more than “complying with the letter of the law”. System rules and government regulations often lag the technology advancements that businesses (and fraudsters) use on a daily basis. While rules and regs often do not require certain controls, at the end of the day it is the obligation to the customer and ultimately the reputation of the business that informs risk mitigation. Going beyond mere compliance often is the better choice, provided the choice is based on study, judgement, and prudence.
For example, e-commerce controls are available and necessary at multiple points in a transaction. But how many controls and where to place them is critical in balancing risk with a smooth customer experience. Some questions to ask when analyzing an ecommerce customer journey include:
- What controls are necessary at login to prevent account takeover (ATO) via bots or more complex attacks?
- What controls are necessary post login as the user journey continues?
- How might rewards, coupons or other incentives entice fraudsters?
- How are fraudster attack vectors used across multiple fraud schemes?
- How can preventative steps in each channel complement one another so that all channels benefit?
These questions highlight the need to employ a cross-functional team in order to identify and to focus on the right tasks. Risk management in particular benefits from coordinated action.
We have pointed out the suboptimal results that stem from siloed perspective and actions. Don’t just look at login page hacks. Include account confirmation pages, checkout, and payment pages. Fraud mitigation is a complex discipline that demands a layered approach. And techniques that worked only last month are quickly circumvented. Hackers are sophisticated. For example, bots that mimic human behavior are commonplace. CAPTCHA controls were initially subverted by fraudster-staffed teams who manually complete these forms when bots cannot. More recently fraudsters are using AI to provide correct responses once thought only possible with human cognition. This is an arms race that demands in depth collaboration.
Hacker Sophistication Demands Cross-Functional Defense
Security requires defense in depth. Hackers have increasingly powerful tools at their disposal, abundant time, zero rules or regulatory oversight, and multiple targets to exploit within your enterprise, each of which is susceptible to various methods of attack.
Building a multi-layered defense is hard. One layer manages who is getting access to your system and what users do as they traverse it. Authentication at login is a first line of defense and it is a target under significant pressure. Account takeover (ATO) attacks, augmented by bots able to emulate human behaviors, are proving to be increasingly effective.
The use of multiple techniques that look not only at the actual login step but also at the behavior on payment confirmation and checkout pages is required. And this e-commerce transaction flow is just one of many possible targets.
Understanding how these attack vectors are used across different fraud schemes is critical to the selection of the right controls. Building an adequate defense requires the participation of those who understand how fraud is conducted and those who understand the applicable technologies. Together, strong procedural and technical controls can result. Otherwise, the enterprise is doomed to play an expensive and losing game of fraud “whack-a-mole.” This is yet another benefit of cross-functional collaboration.
Ask: Should We Keep Doing It This Way?
With the Money Team in place, the power of collaboration can be put to work. And it can start with a review of basic assumptions.
Most decisions made years ago were right at the time. But risk mitigation and security options have expanded significantly in just the last few years. Asking “why are we doing it this way?” is a healthy exercise that, in our payments strategy consulting experience, can improve security. An example of this might be the elimination of merchant-owned systems when outsourced options are available. Oftentimes system and process simplification through automation and outsourcing reduces cost as well as risk..
A rigorous payments process review produces real benefits.
Prove It: To the Auditor and to Yourself
For a time, proof of compliance with the applicable security standards was viewed as sufficient evidence that controls were in place. Yes, demonstration of PCI compliance is an important checklist item for card acceptance security. You have to satisfy your acquirer that your controls are up to snuff.
There are many ways to prove compliance. An entire industry has been built around PCI compliance so that you can demonstrate to your card acquirer and insurer that you meet an external standard. However, as the merchant or biller adds other forms of payment (ACH, PayPal, etc.) different compliance requirements apply, and new security concerns arise. Complexity increases.
Proving risk management strength to yourself is another matter. That process review is a great start. Another step is external validation through penetration testing. You hire “white hat” outsiders to employ the latest hacking tools and tactics in order to reveal the unknown risks compliance testing cannot find. Taking this idea a step further, “red teams” that attempt to game controls via fraud schemes can highlight weaknesses before real fraudsters exploit them. Hopefully.
In the end, the goal is to prove to yourself and your organization that your risk management controls are adequate to meet your company’s ’s risk tolerance.
A Board Level Concern
Risk management and payment security are board level concerns. A breach may cause lasting, and expensive, reputational damage. Legal costs and network fines can mount. An ecommerce retailer that cannot process payments for an hour in December loses real money. It is the Money Team’s responsibility to surface and quantify these risks so that enterprise leadership can direct risk mitigation investments.
The board sets the “tone at the top” and the organization’s risk appetite. Risk in some areas may be worthwhile and in others entirely unacceptable. It’s the board’s job to make those determinations. And to make sure executive leadership carries out the board’s directions.
The Money Team’s work can inform leadership, providing insights into the mechanics, probability, severity, and control options for payments risks.
This Takes Work
This chapter demonstrates risk management’s complexity. That complexity demands cross-functional assessment and mitigation. The knowledge required to meet the challenge goes well beyond that of a single line of business, a single payment method, or organization.
Starting with a thorough risk assessment – risks categorized and characterized – the organization is able to establish a framework for ongoing assessment, reporting, and process improvement. Risk-based resource allocation can then be made. Without that level of leadership and comprehensive, collaborative participation, inefficient implementation of controls is as good an outcome as can be expected.
Risk management and how it fits within a merchant’s payments operations is a major component of Glenbrook’s payments strategy consulting work. Do reach out to get answers to any questions or to discuss your payments roadmap.


